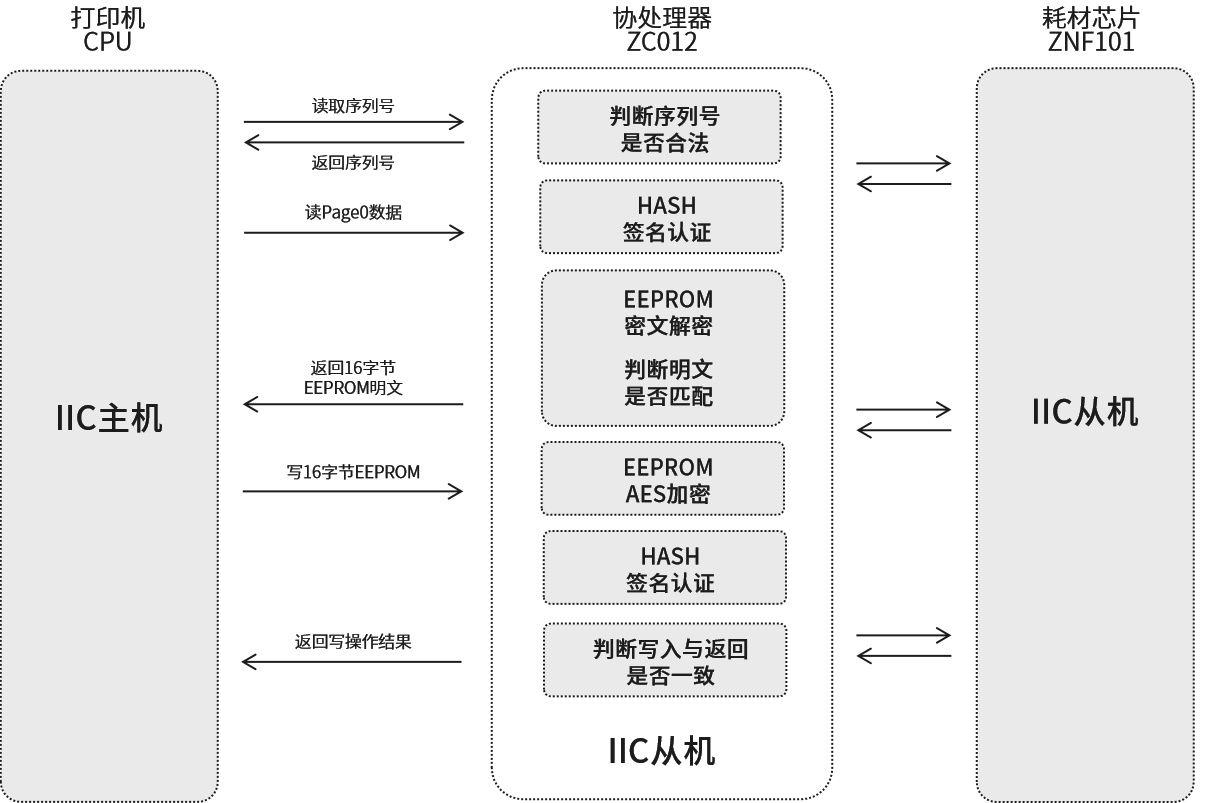
ZC012 anti-counterfeiting security solution is a solution to solve the security certification of (host and) slave machines. It adopts a coprocessor and consumable chip model, and consists of two modules to form a security certification module. A unique identity authentication process is designed between modules, including algorithm signature authentication, communication verification, data verification, etc., and serial number binding design is also made. The design of the module allows customers to quickly replace the original communication solution of the product. The reserved upgrade interface can continuously update the data key of the product and continuously upgrade the product. Ensure the safety of product certification, improve product protection capabilities, and extend product life cycles. Suitable for safety certification needs of a variety of electronic consumable products.
Introduction: Anti-counterfeiting authentication comes from the exchange of data algorithms and identity authentication between two security chips. The coprocessor returns the authentication result to the motherboard CPU. This solution can ensure the security of the entire authentication system and place it on the security chip, reducing the motherboard CPU's security requirements for the chip. Solution module:
High security and difficult to crack: System security is mutually borne by the coprocessor and the consumable chip, making cracking difficult and costly.
Reduce development difficulty: The host only needs 3 instructions to complete data interaction and verification with the consumable chip, greatly reducing development difficulty.
Convenient integration and transplantation: Co-processors and consumable chips do not need to be developed and are plug and play for easy integration and transplantation.
32-byte digital signature: The digital signature is obtained through the HASH algorithm calculation of the serial number, random number, counter and internal key, making the data unable to be tested and copied.
HASH/Symmetry: Symmetric algorithm is used to encrypt data, asymmetric encryption algorithm is used for data transmission and interaction, and HASH algorithm is used for digital signature authentication.
8-byte serial number: A unique 64-bit serial number that participates in encryption and signature authentication of data interactions to ensure that data is copied and cannot be used
256-bit random number: Exchange of random numbers between master and slave machines ensures that the data stream transformation of each data exchange is not repeated, preventing side channel attacks and digital signature counterfeiting
Reserve upgrade interfaces, continue to upgrade products data keys, continue to update products, regularly eliminate exposed chip data and encryption technology, and continue to maintain product protection capabilities.

 Contact us
Contact us